
Using Aws Systems Manager Session Manager Kernel Talks
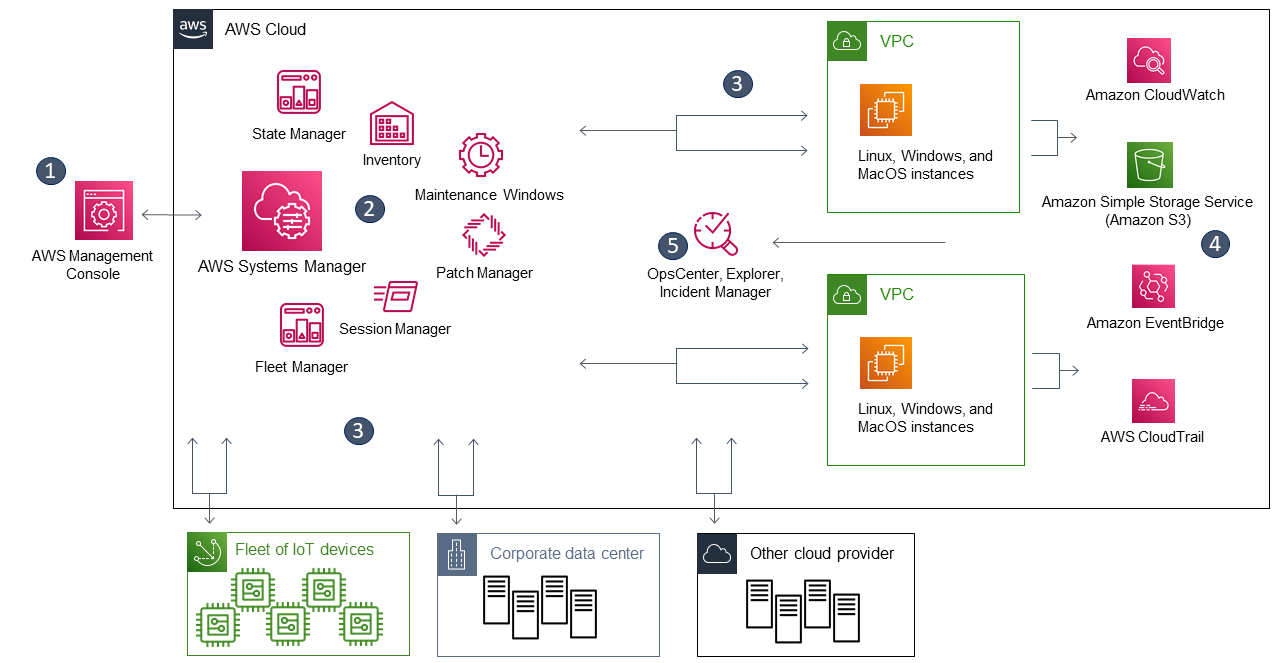
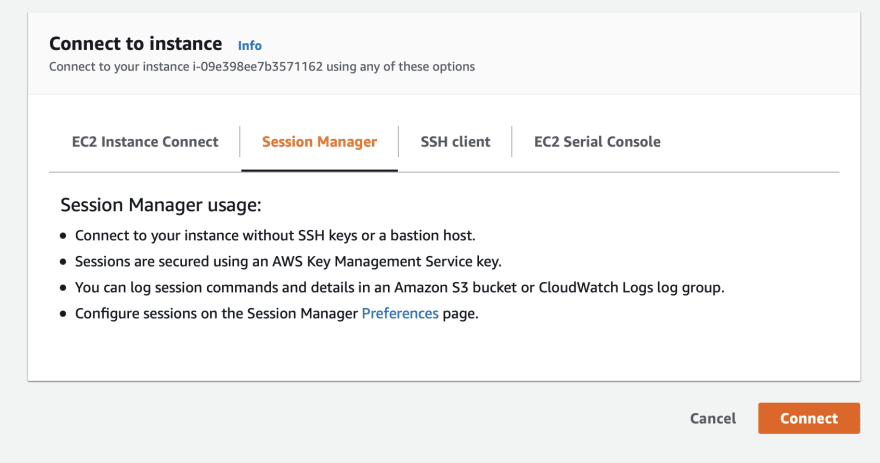
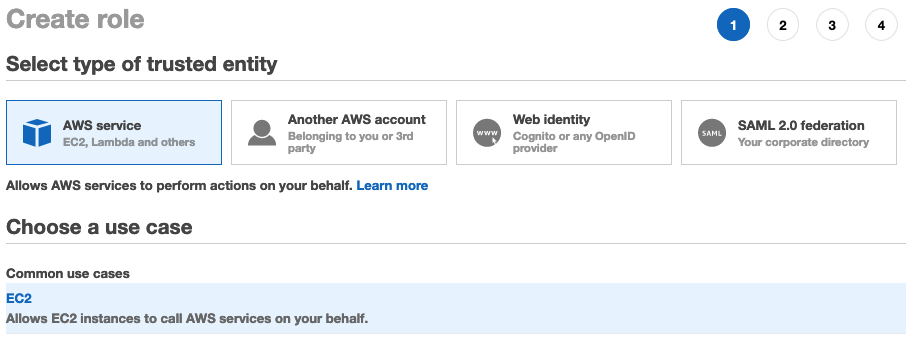
Session Manager is a fully managed AWS Systems Manager capability that lets you manage your Amazon EC2 instances through an interactive oneclick browserbased shell or through the AWS CLI If an instance profile that contains the AWS managed policy AmazonSSMManagedInstanceCore is already attached to your instances, the required SSM(AWS Systems Manager)のSession Managerで、KMS encryption(暗号化)すると上記のhandshakeエラーが出ます。 無効化するとprivate subnet経由でシェルアクセスできます。 SSM Agent バージョン 3022 、AmazonLinux2です。 awscli/0 Python/2718 Linux/amzn2x86_64
Amazonssmmanagedinstancecore session manager
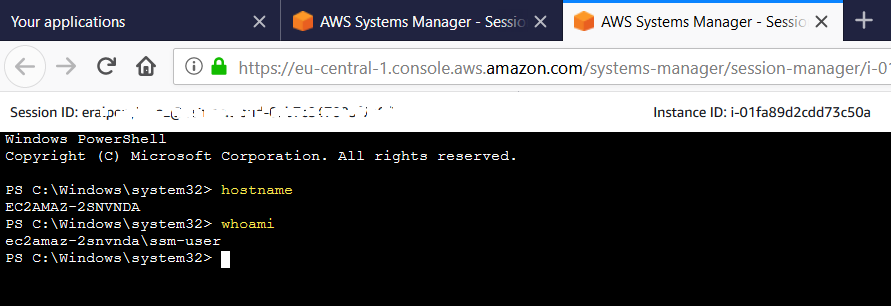
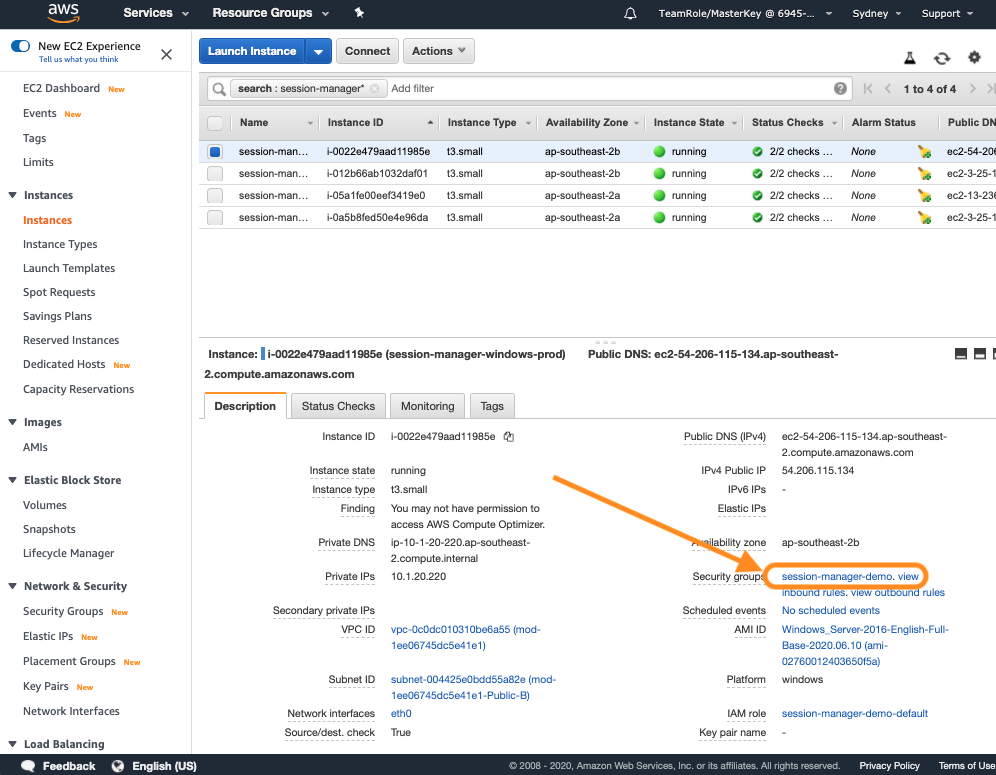
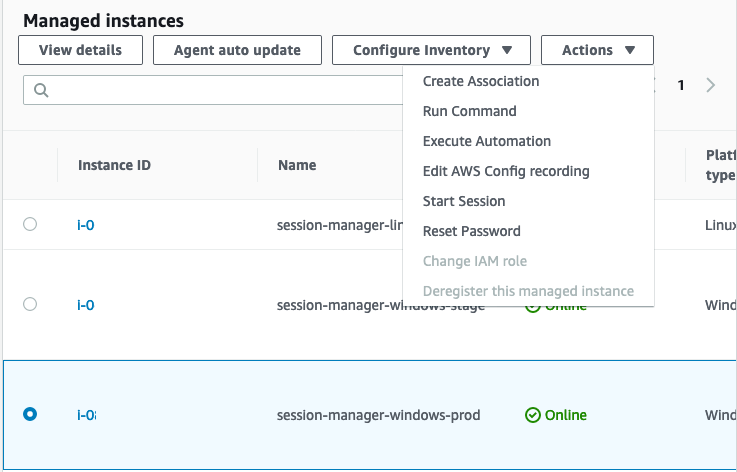
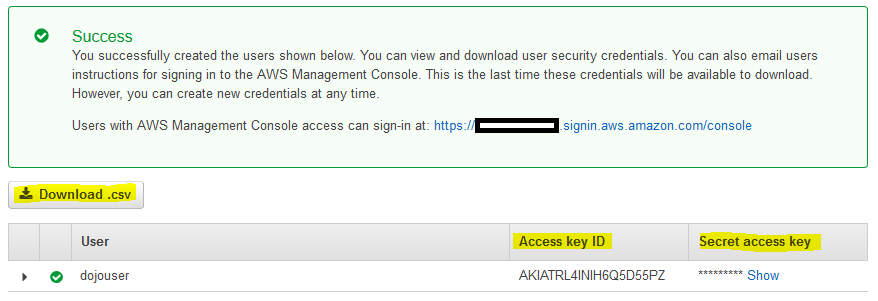
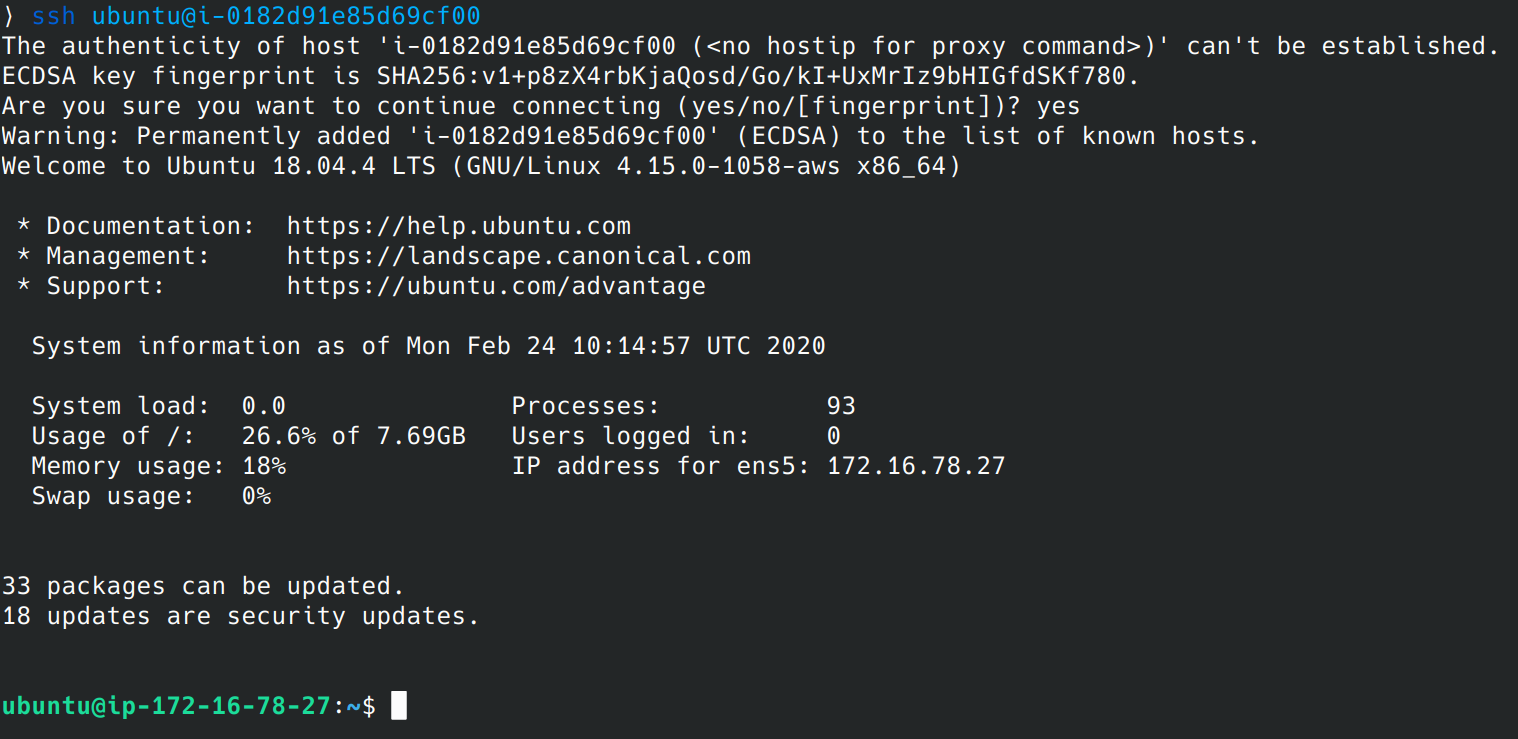
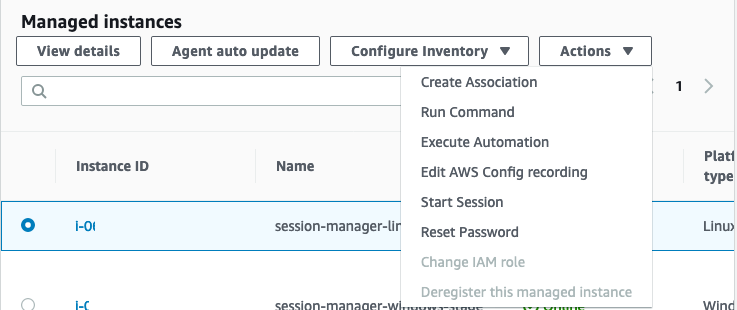
Amazonssmmanagedinstancecore session manager-Session Manager Inventory Stuck in Pending State technical question AmazonSSMManagedInstanceCore and AmazonSSMPatchAssociation Next, I create a new EC2 instance, t4gmicro with Amazon Linux 2 AMI (HVM) Kernel 510, SSD Volume Type, 64bit (Arm), which has the SSM agent installed by default When I create it, I associate theSessionmanagerplugin Response "The Session Manager plugin was installed successfully Use the AWS CLI to start a session" 5 Finally, establish a Session to connect to your Instance Get your instance id from the AWS console, and start a session to your Ec2 instance
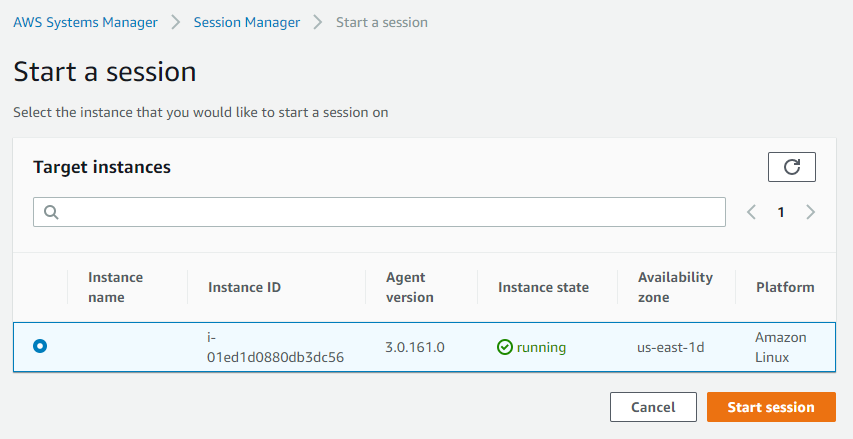
Using Aws Systems Manager Session Manager Kernel Talks
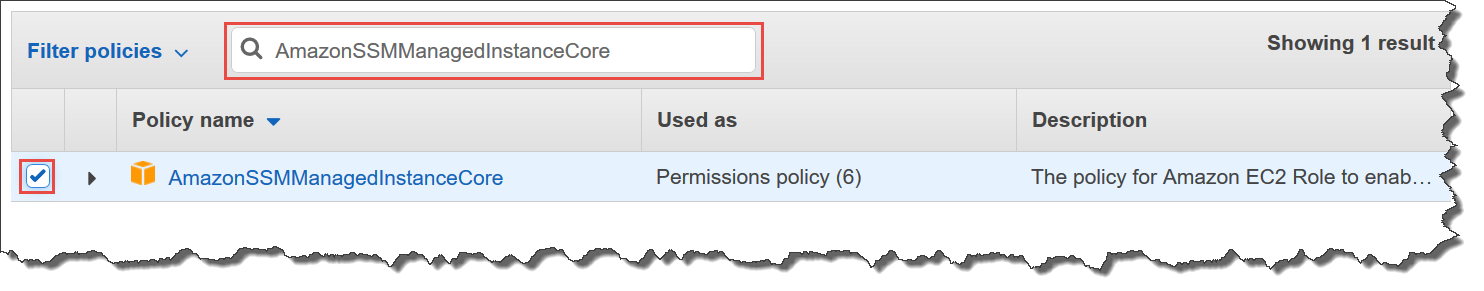
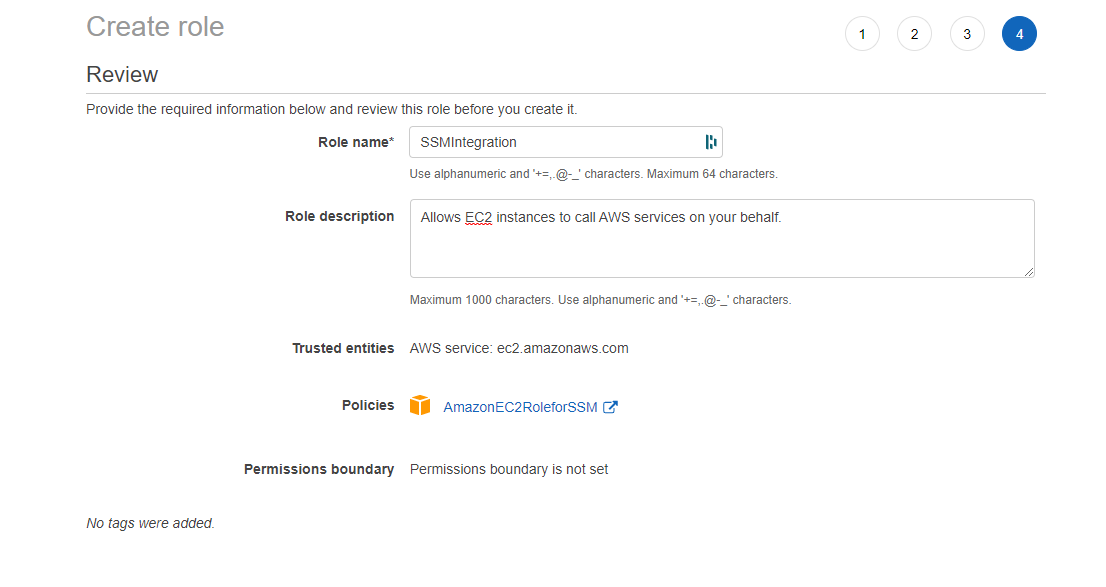
The AmazonSSMManagedInstanceCore managed policy doesn’t include these permissions, so they must be added manually prior to using Session Manager As part of the prerequisites, you should have already set up a role attached with an AWS Managed AmazonSSMManagedInstanceCore policy and used it as the IAM Role for your EC2 Instances 今回は「Session Manager (SSM) を使って EC2 へアクセスする方法 (publicサブネットの場合)」についてまとめます。 この Session Manager を使ってEC2へアクセスできるようになると、 これまで 22ポート (SSH) を開放していたものが解放しなくてよくなります 。 またIt means that you can open an SSH shell using the AWS Console in your browser Select the EC2
This policy should allow working with SSM While I can start and open a session for tunnel forwarding via AWS CLI with the first instance, I cannot do the same for the second one, and I don't understand why When I start the first instance, I see it under the target instances in the session manager If I do it for the second one, this isn't theUse attachrolepolicy as follows to allow the service role you just created to create a session token The session token gives your managed instance permission to run commands using Systems Manager Note The policies you add for a service profile for managed instances in a hybrid environment are the same policies used to create an instance profile for Amazon Elastic Compute sudo dpkg i sessionmanagerplugindeb Verify the installation status ;
Amazonssmmanagedinstancecore session managerのギャラリー
各画像をクリックすると、ダウンロードまたは拡大表示できます
 Aws Systems | 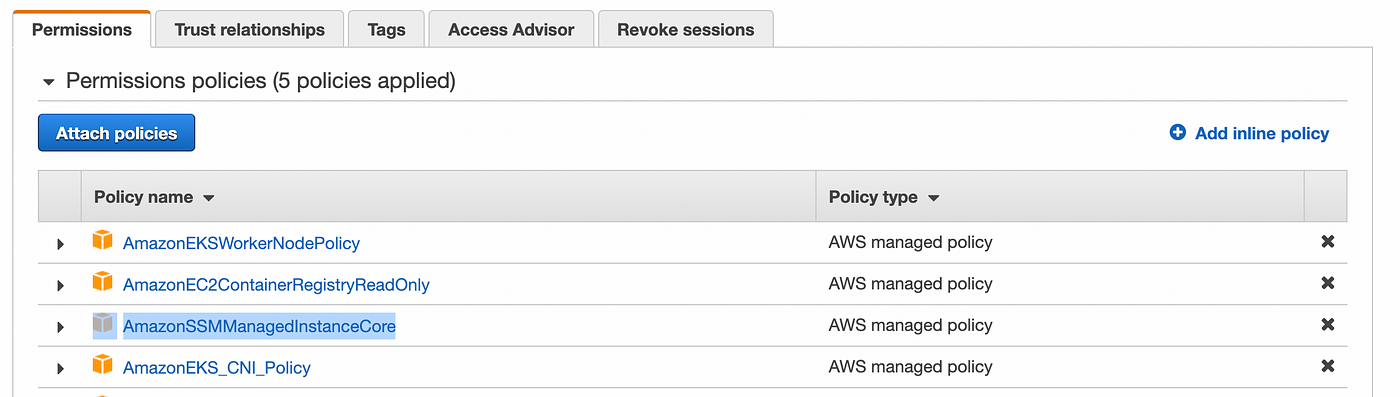 Aws Systems |  Aws Systems |
 Aws Systems | Aws Systems |  Aws Systems |
 Aws Systems |  Aws Systems | 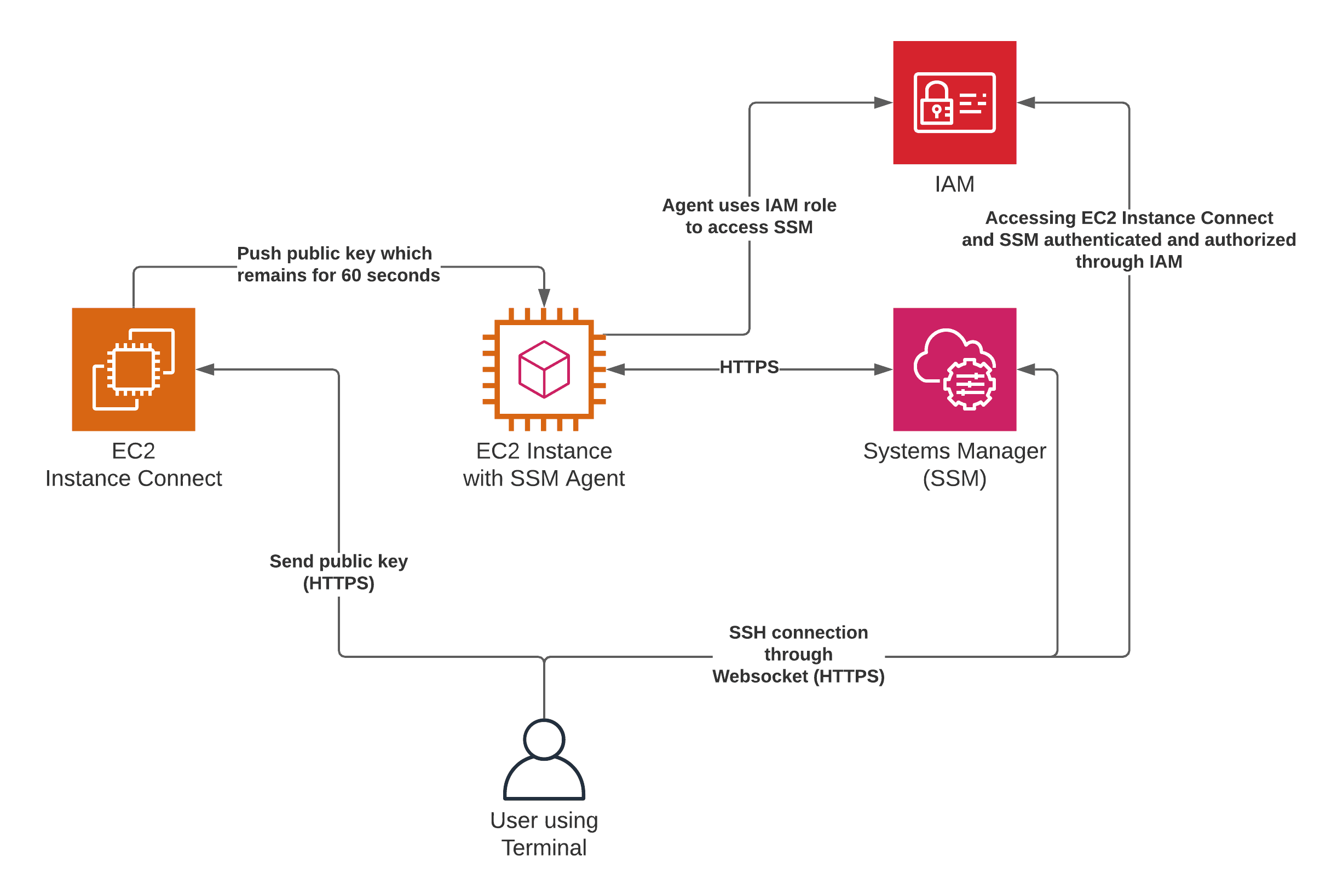 Aws Systems |
Aws Systems |  Aws Systems |  Aws Systems |
 Aws Systems | 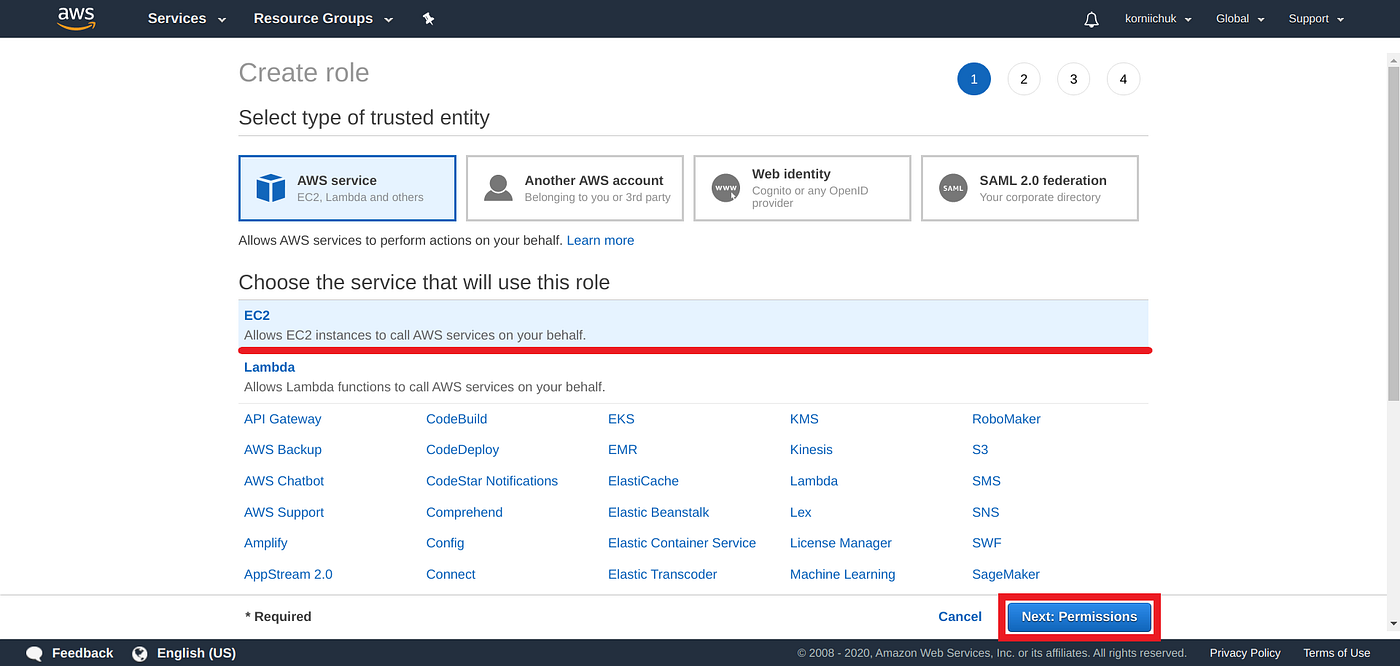 Aws Systems |  Aws Systems |
Aws Systems |  Aws Systems | 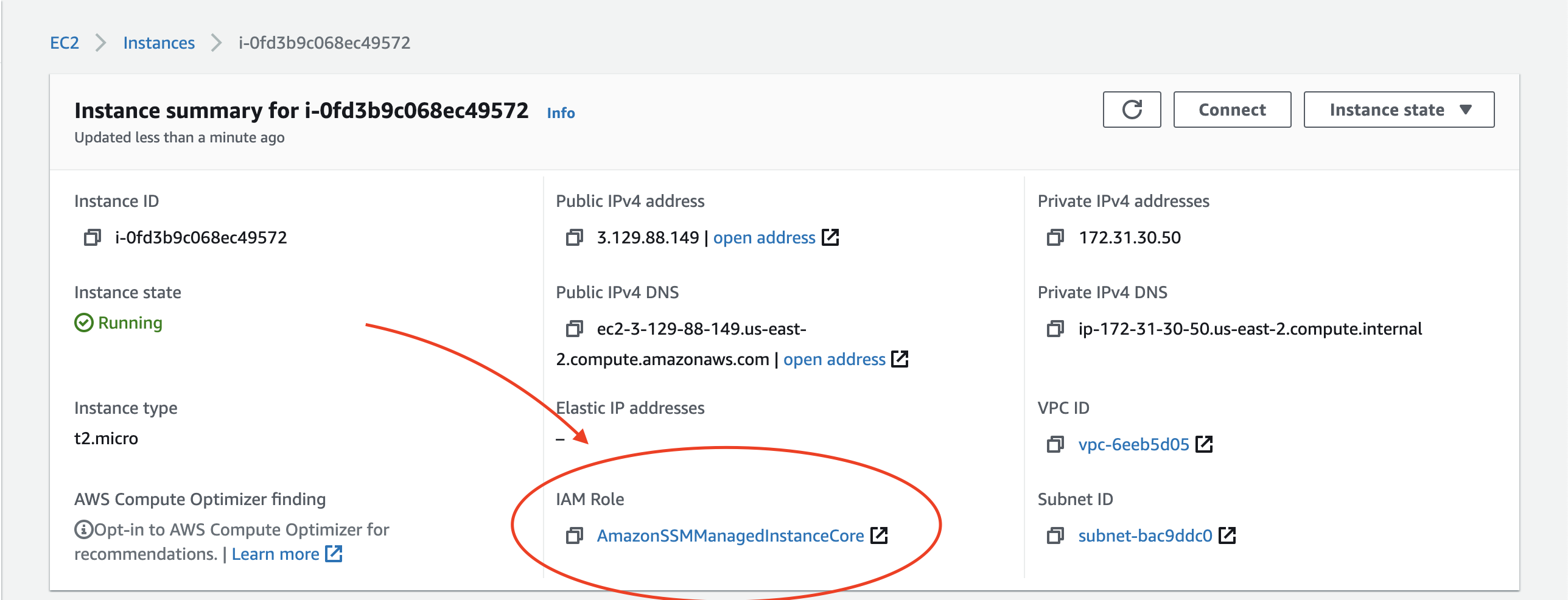 Aws Systems |
 Aws Systems | Aws Systems | Aws Systems |
Aws Systems |  Aws Systems |  Aws Systems |
 Aws Systems |  Aws Systems | 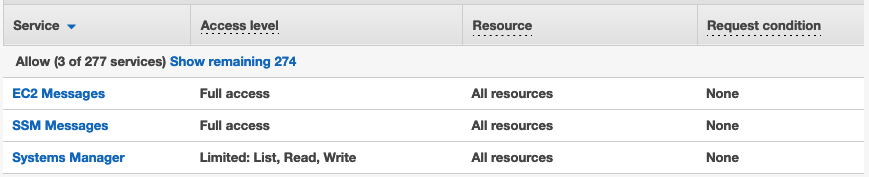 Aws Systems |
 Aws Systems | 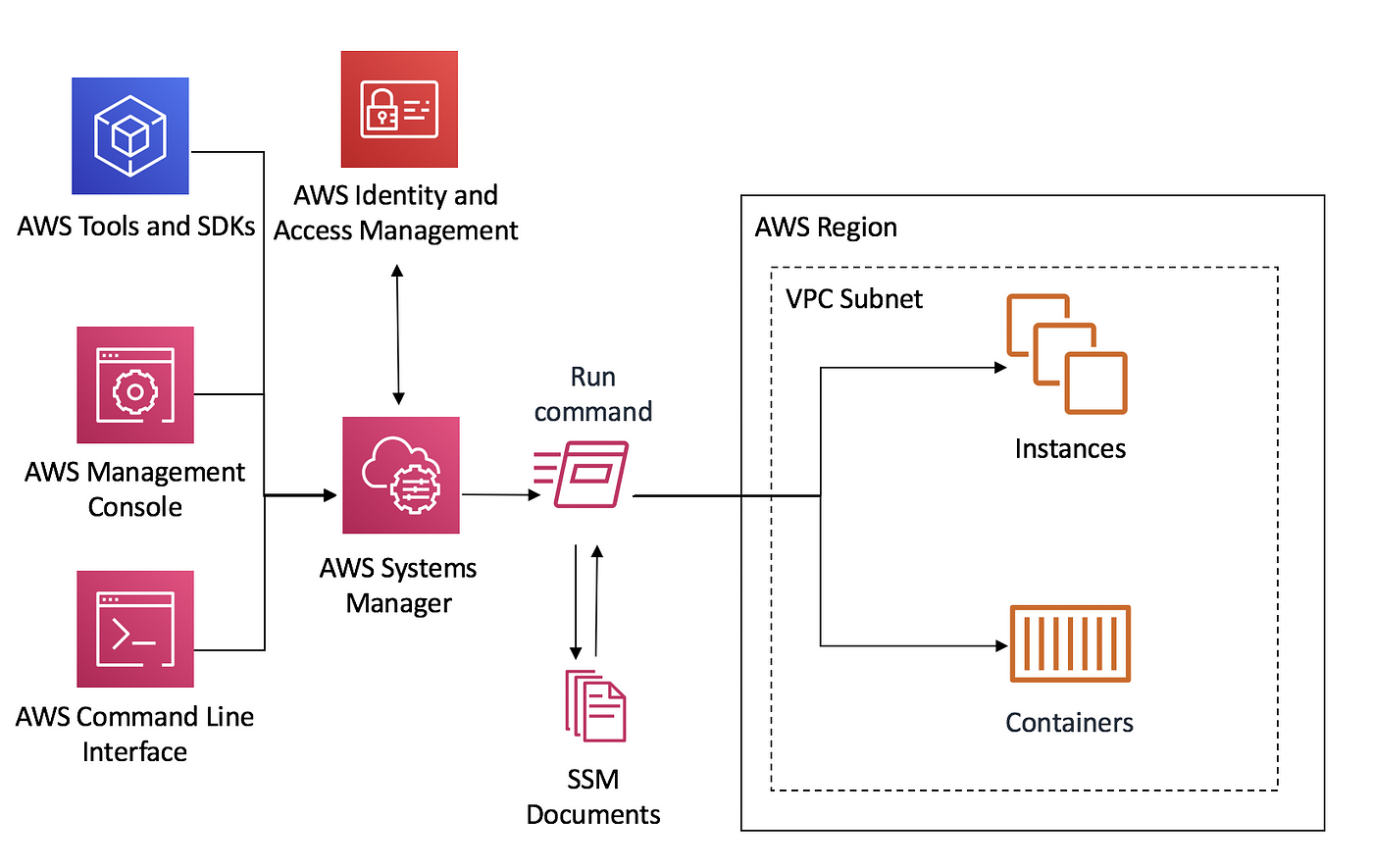 Aws Systems | 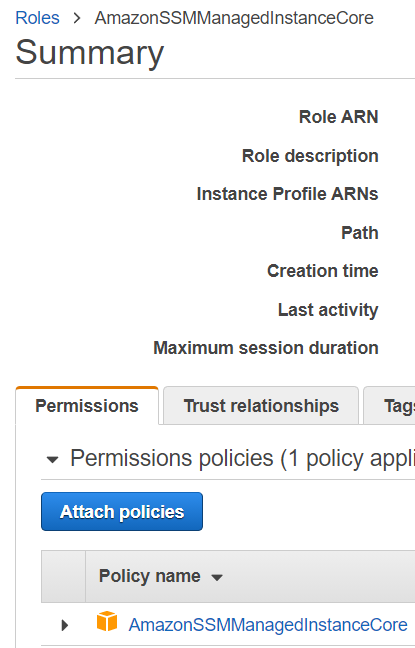 Aws Systems |
 Aws Systems | 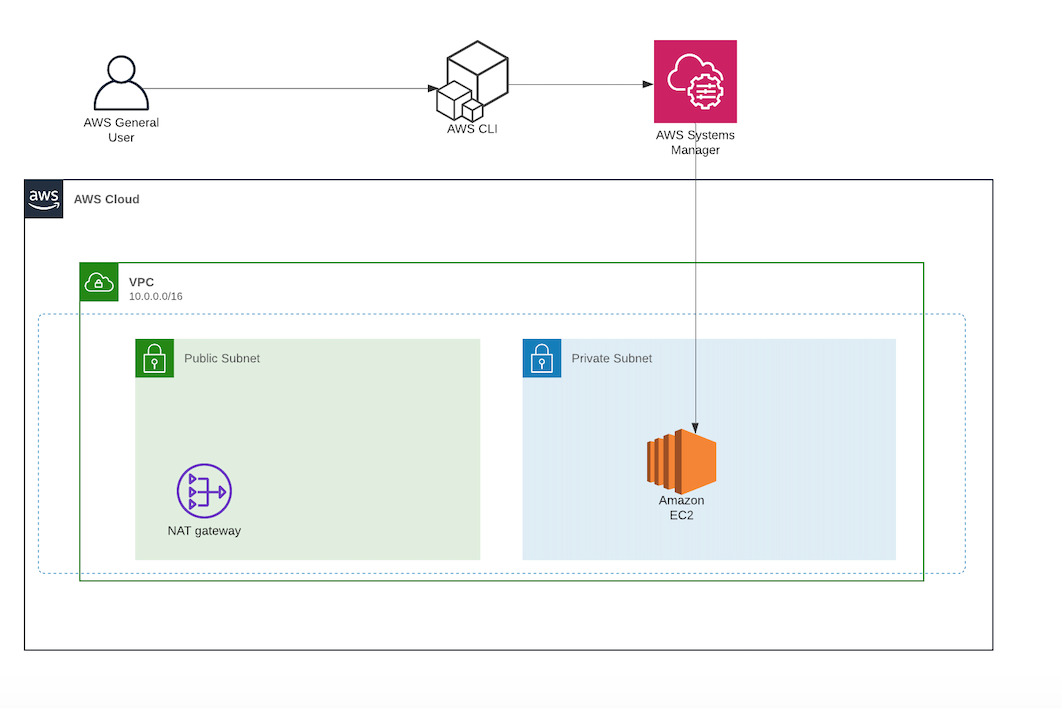 Aws Systems | Aws Systems |
 Aws Systems |  Aws Systems |  Aws Systems |
 Aws Systems | Aws Systems |  Aws Systems |
 Aws Systems | 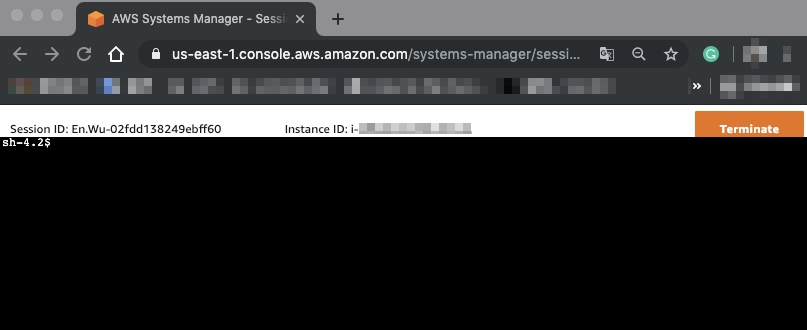 Aws Systems |  Aws Systems |
 Aws Systems |  Aws Systems |  Aws Systems |
 Aws Systems |  Aws Systems |  Aws Systems |
 Aws Systems |  Aws Systems | 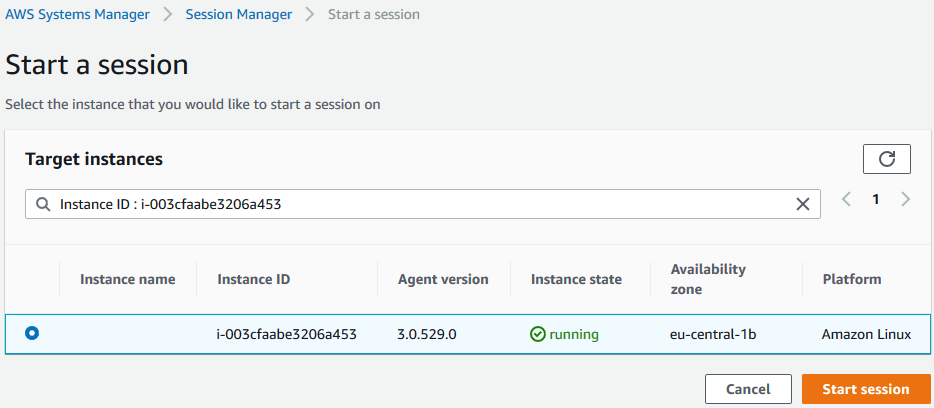 Aws Systems |
 Aws Systems |  Aws Systems |  Aws Systems |
 Aws Systems | 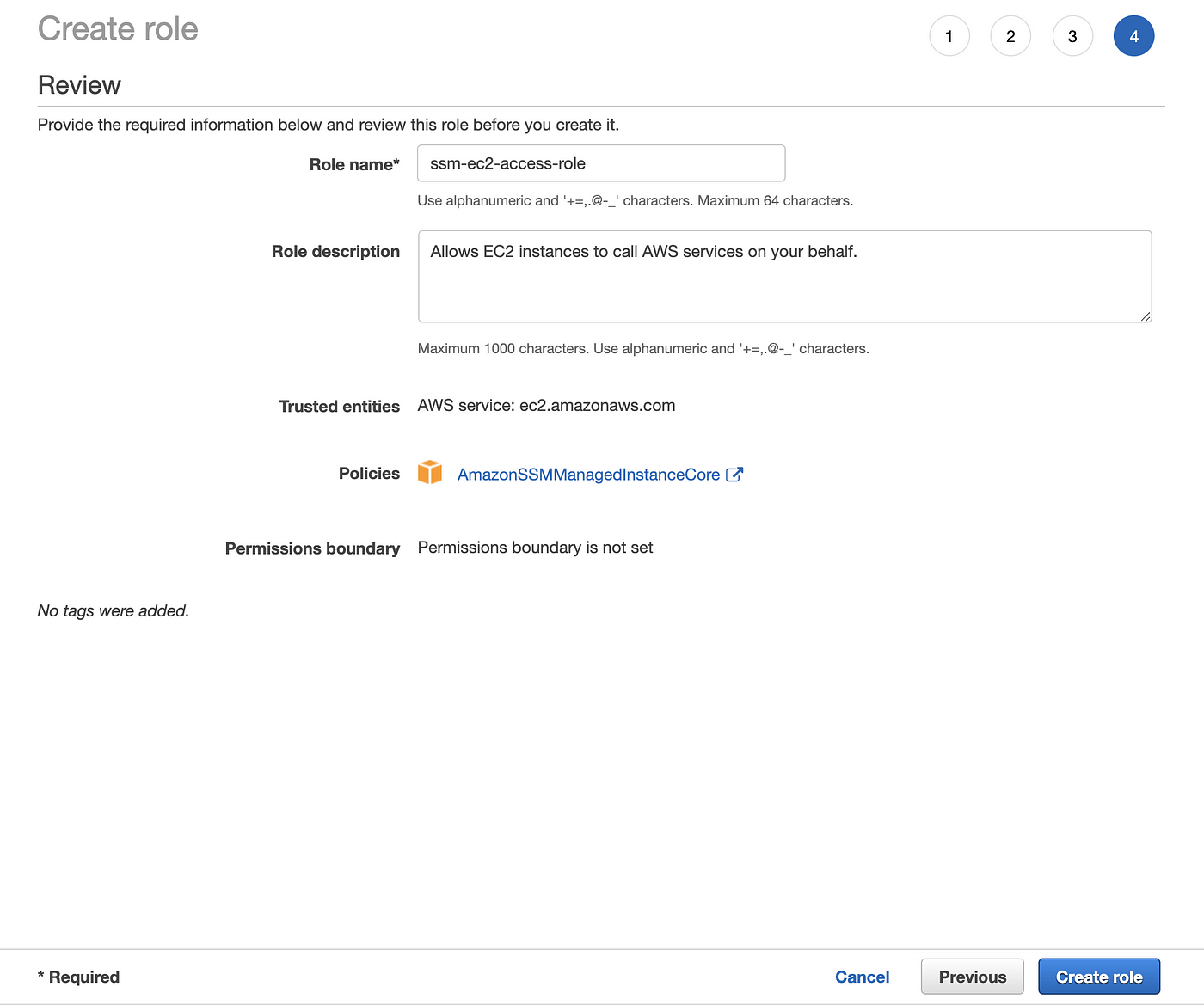 Aws Systems | 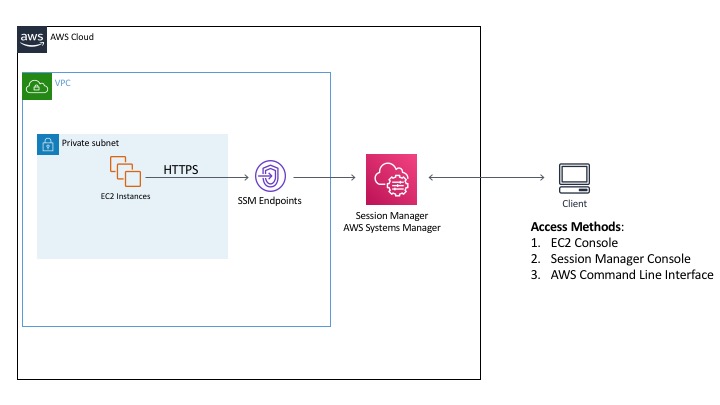 Aws Systems |
Aws Systems |  Aws Systems | Aws Systems |
 Aws Systems | Aws Systems |  Aws Systems |
 Aws Systems |  Aws Systems | 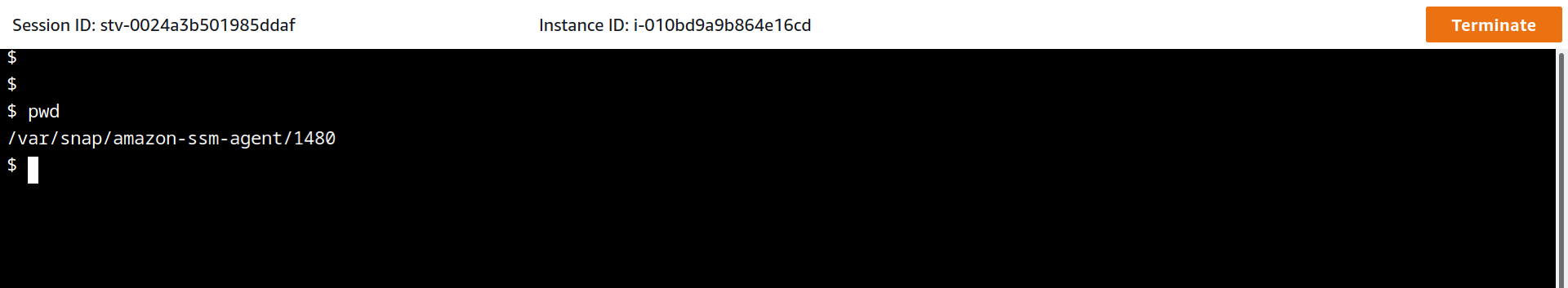 Aws Systems |
Aws Systems | 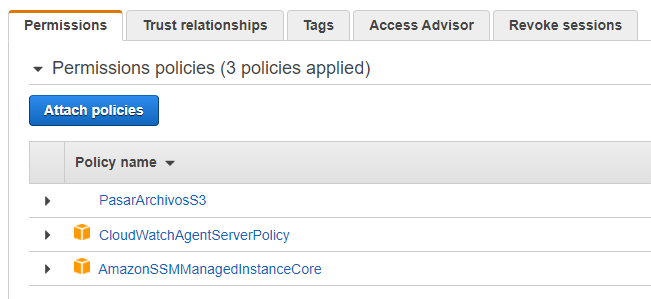 Aws Systems | 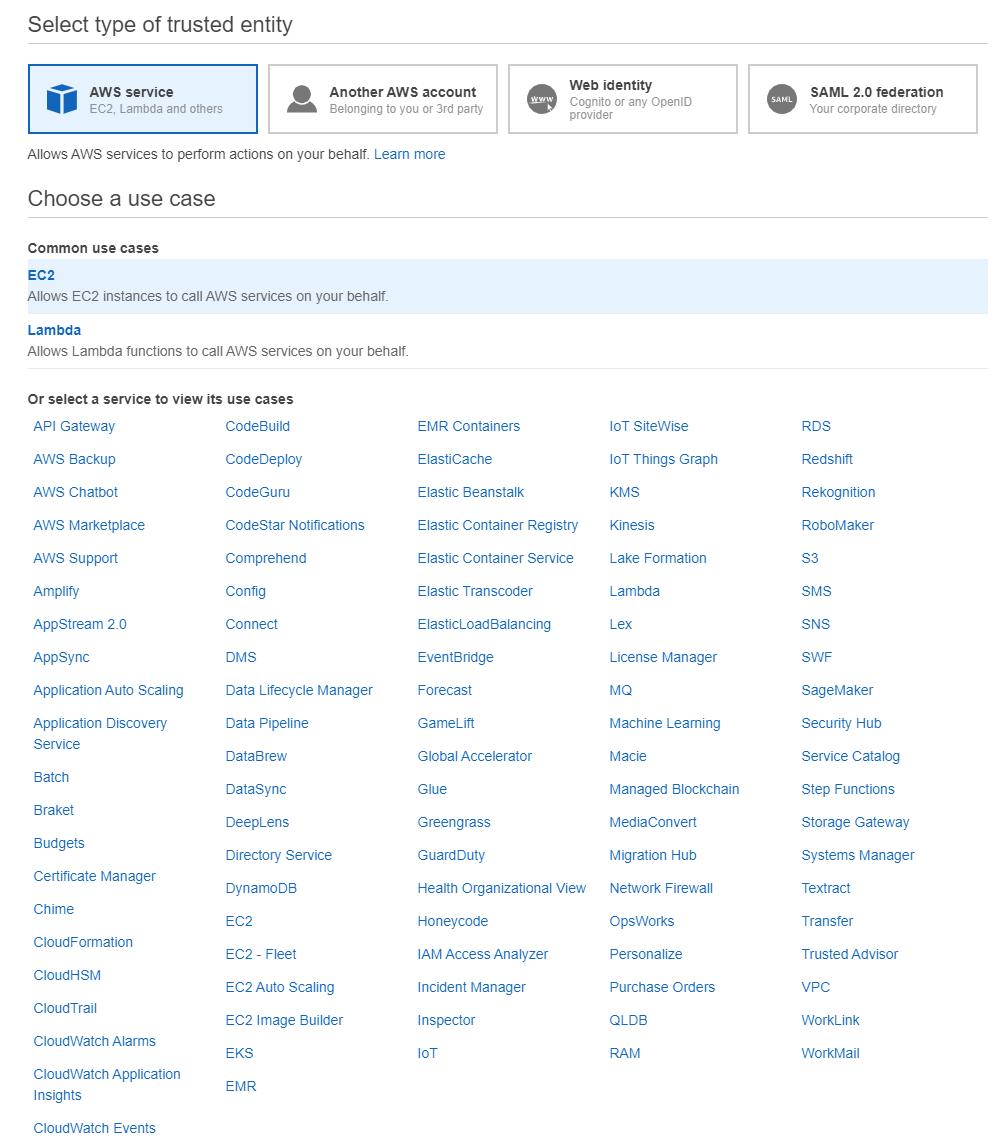 Aws Systems |
 Aws Systems |  Aws Systems | 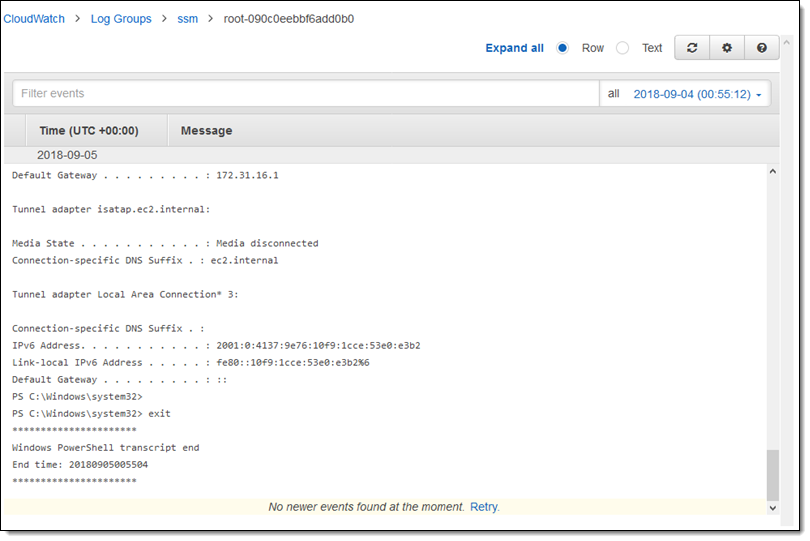 Aws Systems |
 Aws Systems |  Aws Systems |  Aws Systems |
 Aws Systems |  Aws Systems |  Aws Systems |
 Aws Systems | 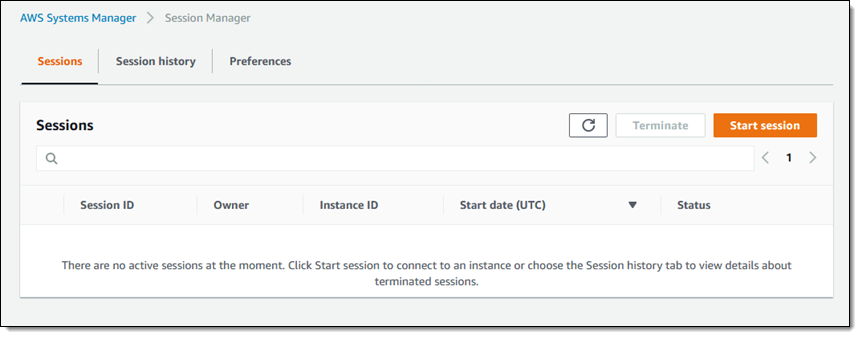 Aws Systems | Aws Systems |
Aws Systems | 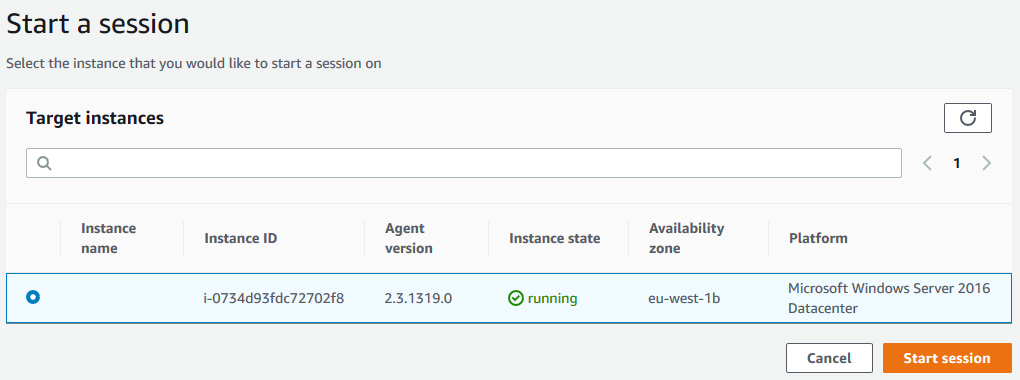 Aws Systems | 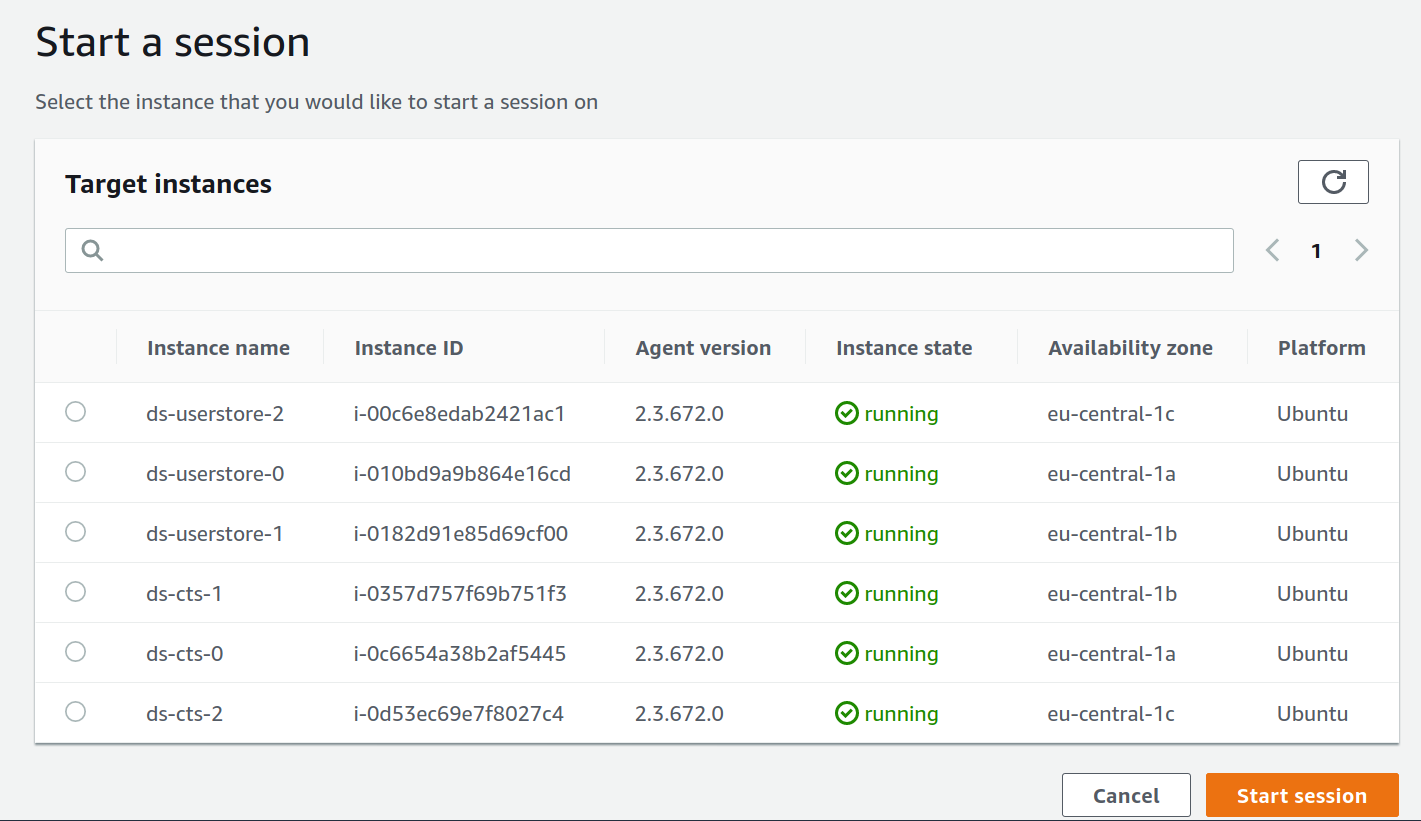 Aws Systems |
Aws Systems |  Aws Systems |  Aws Systems |
Aws Systems |  Aws Systems | 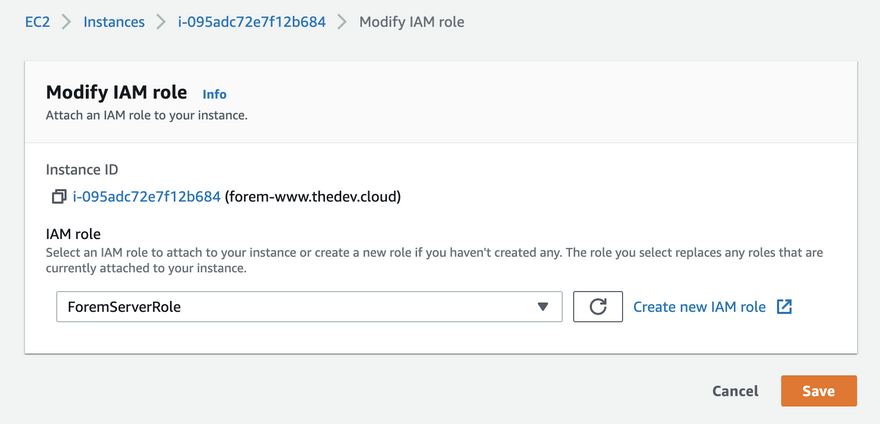 Aws Systems |
 Aws Systems |  Aws Systems | 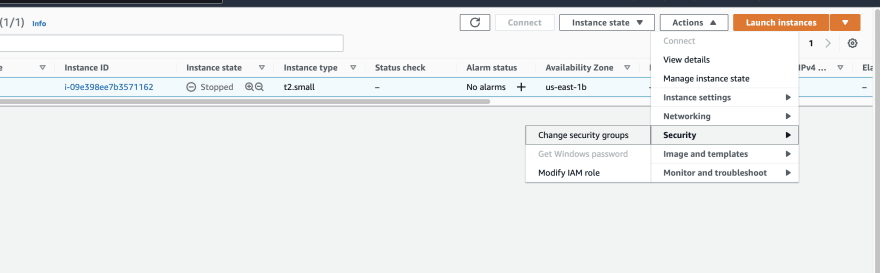 Aws Systems |
 Aws Systems |  Aws Systems | 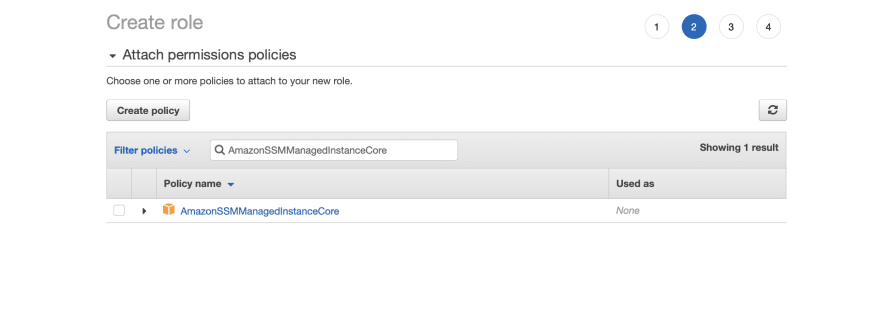 Aws Systems |
 Aws Systems |  Aws Systems | 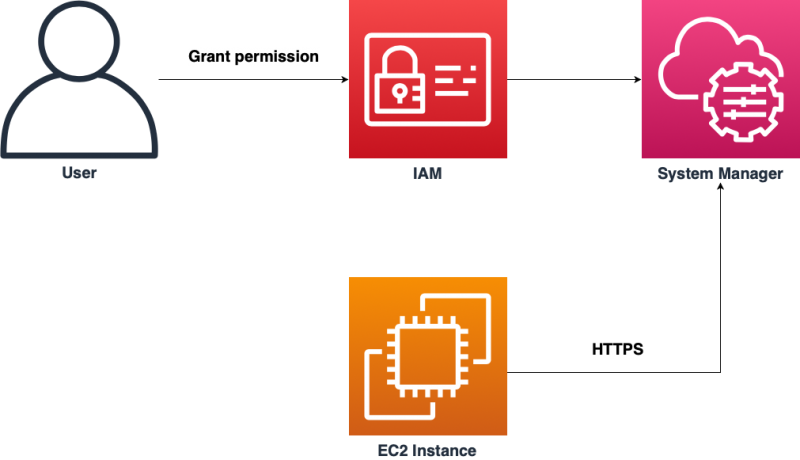 Aws Systems |
 Aws Systems |  Aws Systems |  Aws Systems |
 Aws Systems |  Aws Systems |
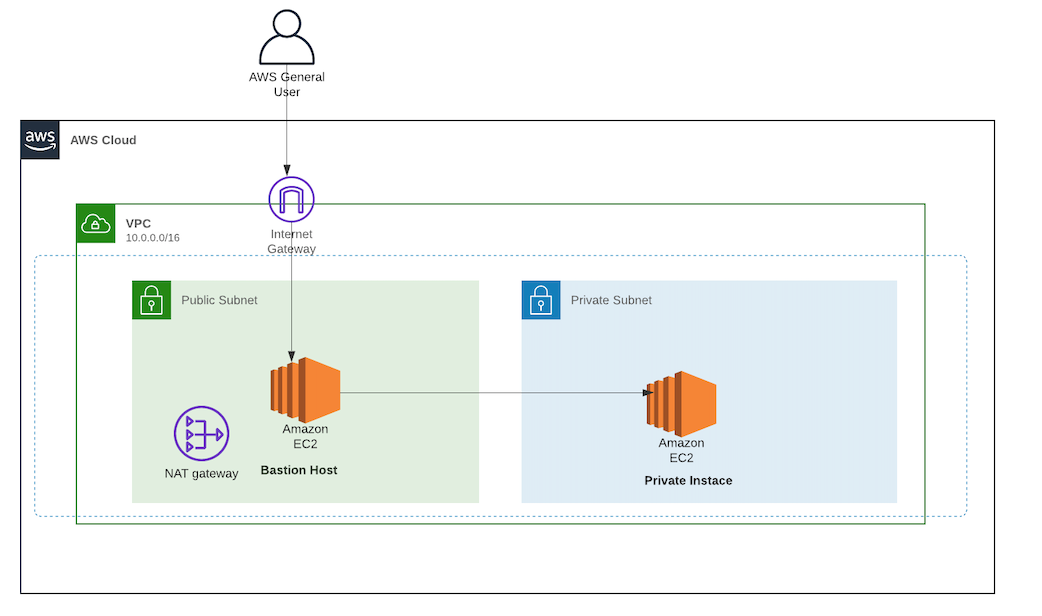
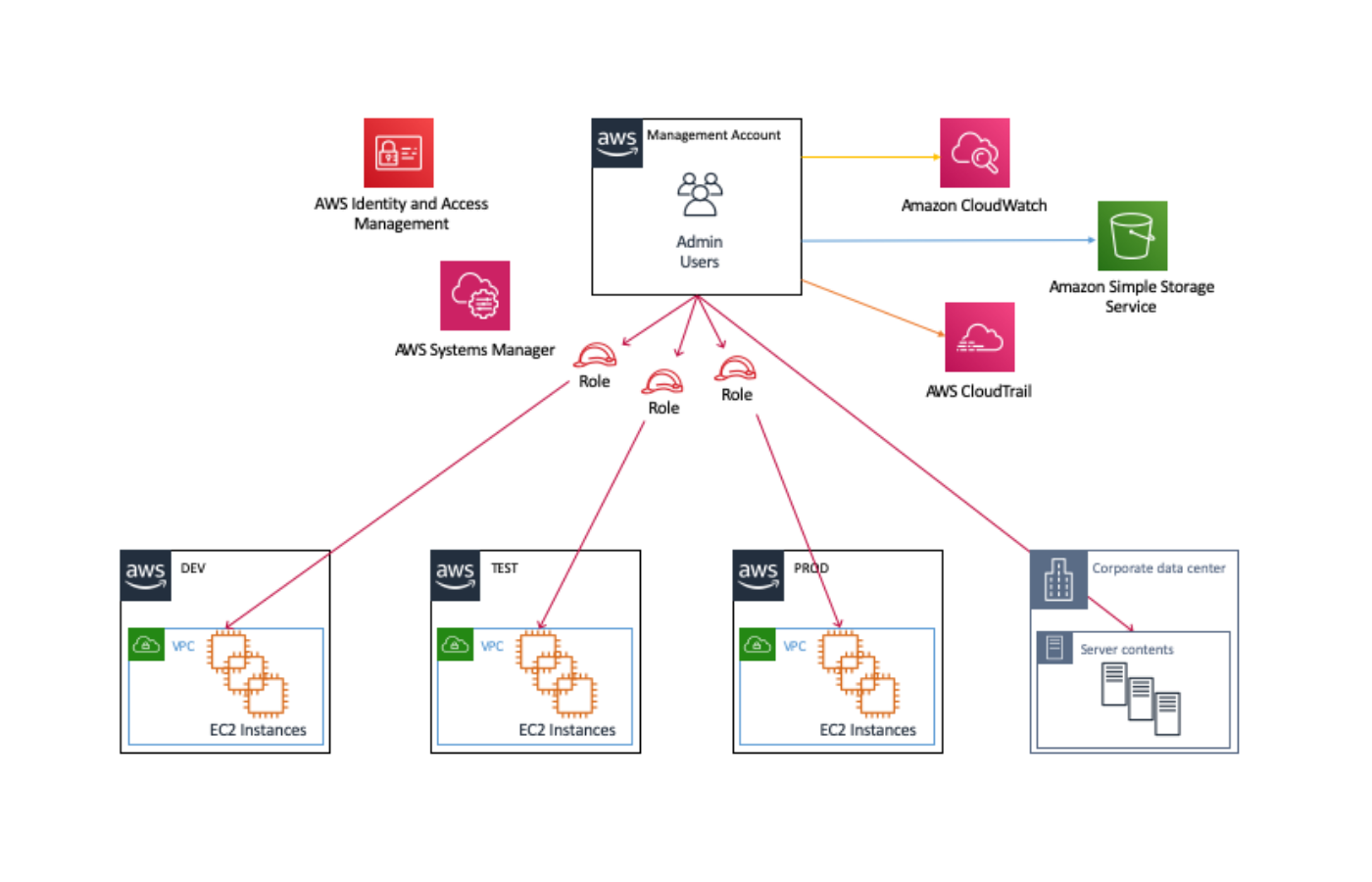
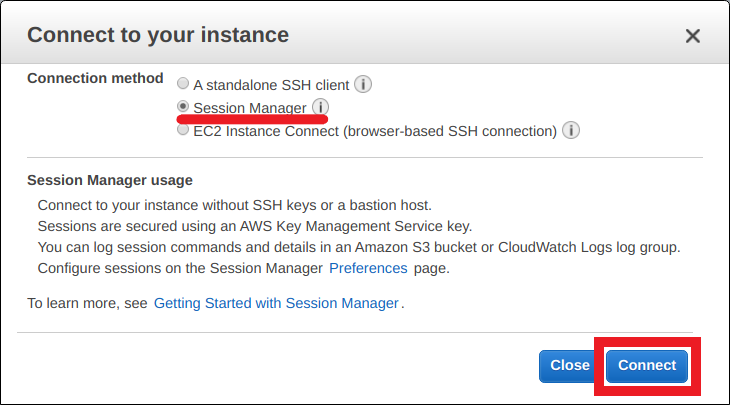
Session Manager を使ってEC2へアクセスできるようになると、これまで 22ポート (SSH) を開放していたものが解放しなくてよくなります。 また、実質的な踏み台サーバーを AWS が提供していることになるので、踏み台も準備不要になってちょっと便利になります。This is the IAM service role for Systems Manager This role grants AWS Security Token Service (AWS STS) AssumeRole trust to the Systems Manager service The AssumeRole action returns a set of temporary security credentials (consisting of an access key ID, a
Incoming Term: amazonssmmanagedinstancecore session manager,




No comments:
Post a Comment